- cross-posted to:
- longreads@sh.itjust.works
- cross-posted to:
- longreads@sh.itjust.works
This is a very entertaining and educational article, giving insights into the methods used by thiefs to try and get access to your phone data.
I don’t like Apple but it’s great that their security is so good when it comes to this.


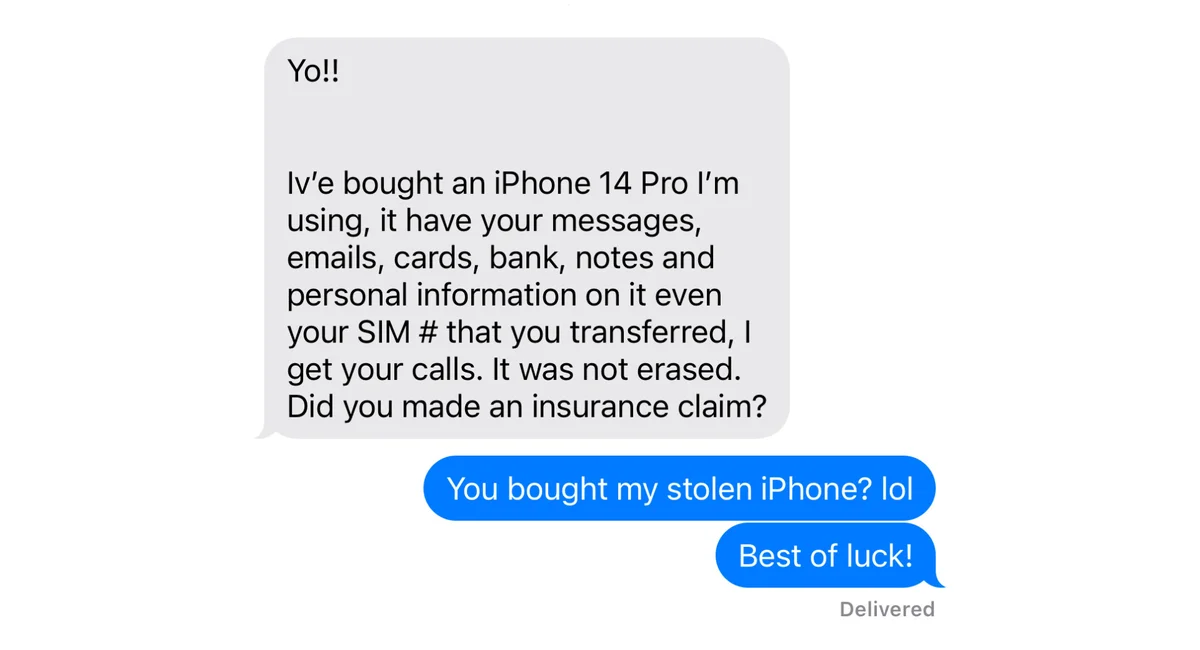
IT was the owner and obviously consented to their own actions.
You didn’t read the post.
You pretty much MUST use paid mobile device management tools to set up and administer company owned Apple hardware, and those tools are notoriously annoying and often just bad
MDM would have been used regardless of OS.
Read again - for most other devices there are cheap and often some free administration tools that small businesses can use. And for many devices they can just reinstall them. But for Apple devices pretty much everything is expensive or very limited.