- cross-posted to:
- longreads@sh.itjust.works
- cross-posted to:
- longreads@sh.itjust.works
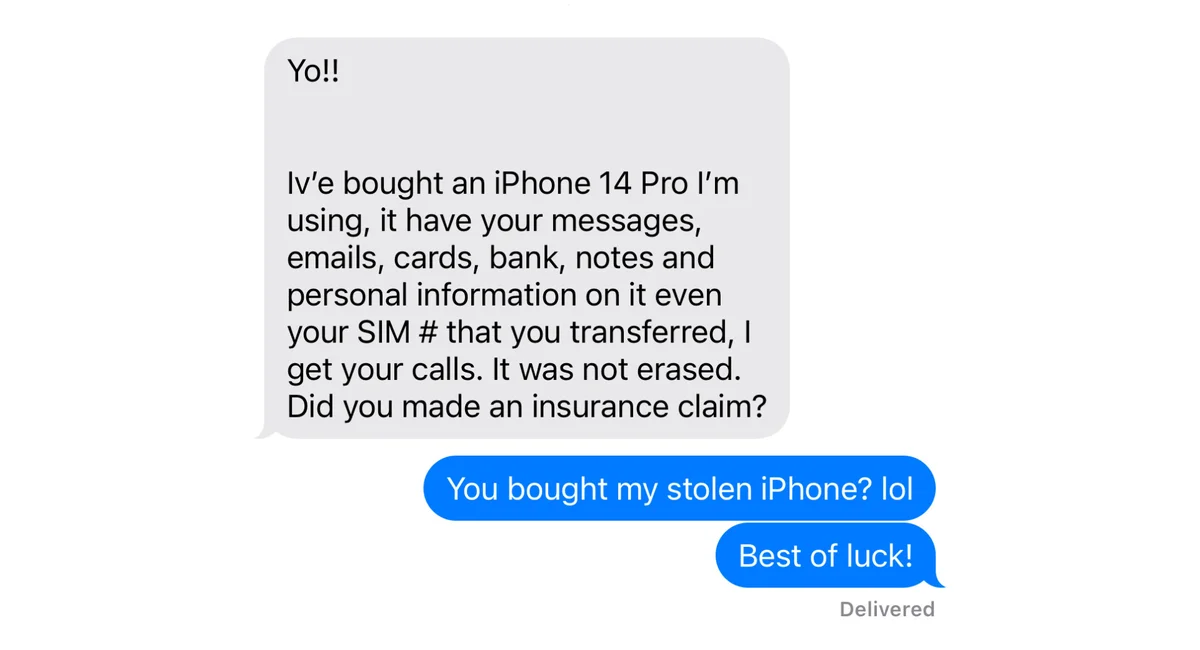
This is a very entertaining and educational article, giving insights into the methods used by thiefs to try and get access to your phone data.
I don’t like Apple but it’s great that their security is so good when it comes to this.


Except you can more easily wipe the os at a low level and fully factory reset the device. That’s not possible with iPhones.
Afaik, that changed a while ago. Nowadays, it should still ask for the google account of the most recent owner.
yeah, factory reset protection, it wipes the user data, but will refuse to fully finish setting up the the os after the reset until the google acct is verified…
Funny thing, even if you do that you can be prevented from initializing the device. You get a “this phone was reset in an unusual way, sign in to the original account used for setup” message the may or not hint at an email address. I’ve got a stack of them on my desk from former employees that I’m trying to get back into. Pain in the ass for business, good for consumers.
You can’t do that on modern phones with locked bootloader. This is the reason why manufacturers who allow bootloader unlock still don’t ship phones with bootloader unlocked by default.